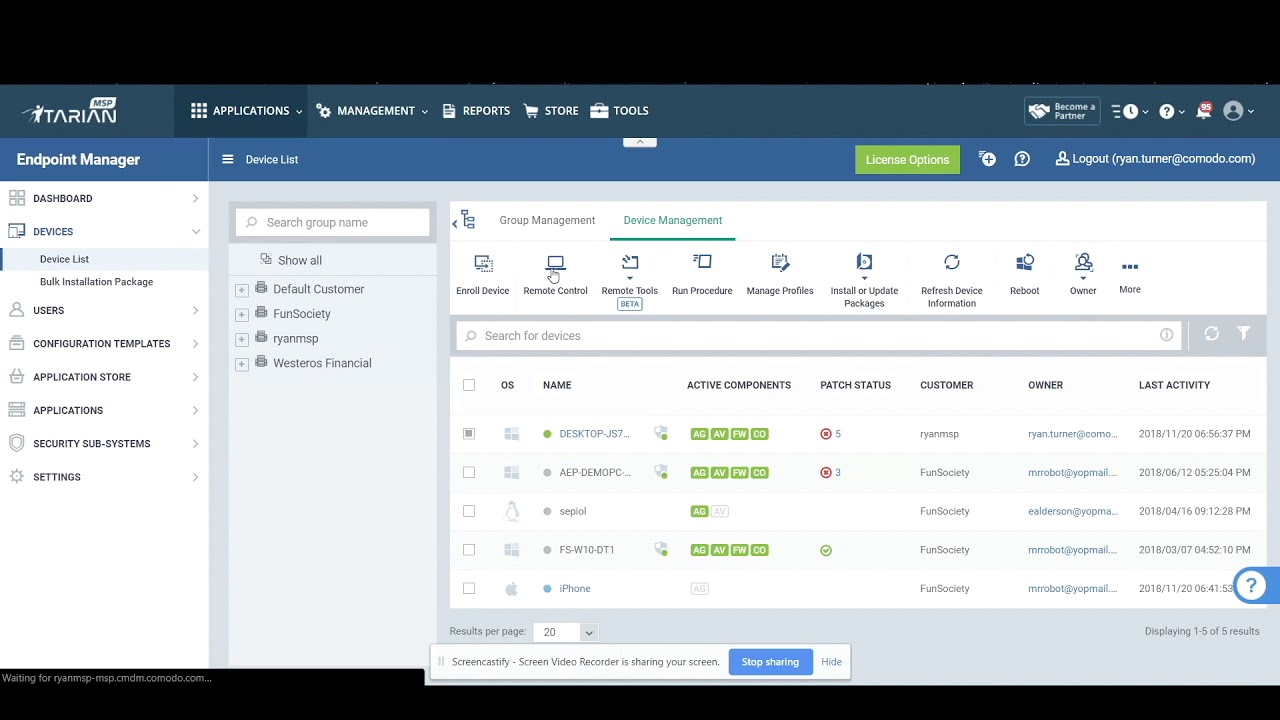
Selecting an RMM System for Growth
Selecting an RMM system that aligns with your company’s growth strategy and future needs is crucial for sustained success. Choosing the right system isn’t just about managing your current IT infrastructure; it’s about anticipating future demands, scaling efficiently, and ensuring your technology supports – not hinders – your ambitious goals. This guide will walk you … Read more